Cybersecurity threats, especially ransomware, are constantly evolving, so it’s important to regularly audit your ESXi hosts to ensure they have the proper protections enabled. Today I want to share a simple but effective PowerCLI script, Get-RansomwareProtectionStatus, that quickly checks your VMware hosts for important ransomware-related security configurations.
🚀 What This Script Does
This script focuses on three key settings that enhance protection against ransomware on your ESXi hosts:
- Encryption Mode: Checks whether TPM-based encryption is active.
- Secure Boot Enforcement: Confirms Secure Boot is enabled.
- Exec-Installed-Only Mode (Configured & Runtime): Ensures only binaries from installed VMware VIB packages can execute.
Having these settings properly configured greatly reduces the risk of unauthorized code execution—exactly what you want to fight ransomware!
🔧 How to Use the Script
Here’s how simple it is. First connect to your vCenter and then run a script.
.\Get-RansomwareProtectionStatus.ps1 <HOST>It generates a clear, colored summary, instantly telling you what’s secure and what needs your attention.
.\Get-RansomwareProtectionStatus.ps1 fs-vsan-05.int.dc5.cz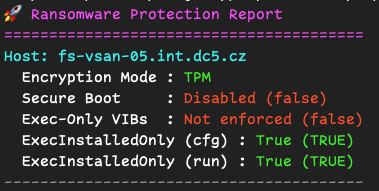
Green means you’re good; red ? You’ve got work to do! Look to the official documentation:
🛠️ Customize and Automate It
You can integrate this script into your monitoring routines, run it on multiple hosts with automation tools like Ansible Semaphore or GitLab CI, or even schedule regular audits.
⚡ Pro Tip: Save your reports to a file or push results directly to your monitoring dashboard to track security over time!
📦 Get the Script
Check out the script in my GitHub repo [link here] and let me know your thoughts! Direct link to script [here]
Feel free to comment or ping me on social media if you’ve enhanced it further or found a creative use case. Stay secure! 🛡️
