Managing encryption across multiple ESXi hosts can be a bit of a hassle. But don’t worry. I’ve got a simple PowerCLI script that’ll save you time and headaches by quickly retrieving encryption status and recovery keys from your VMware environment.
Why Do You Need This?
Ensuring your ESXi hosts are correctly encrypted is essential for security. Regular checks help prevent surprises later, especially during troubleshooting or audits.
Getting Started
First, make sure you’re connected to your vCenter:
Connect-VIServer -ServerReplace with your vCenter IP or FQDN.
The Script Breakdown
Here’s a quick rundown of the PowerCLI script to verify encryption settings across all ESXi hosts and who Recovery key for each ESXi host. (link to GitHub repository and file tpm_recovery_key_backup.ps1):
# Connect to your vCenter server (if not already connected)
# Connect-VIServer -Server <VCENTER_IP_OR_FQDN>
$esxis = get-vmhost | Sort-Object
foreach ($esx in $esxis) {
$key= @()
$enc = @()
if ($esx.ConnectionState -ne "Connected" -and $esx.ConnectionState -ne "Maintenance") {
Write-Host ""
Write-Host "================================================================================" -ForegroundColor Yellow
Write-Host "🚫 SKIPPED HOST" -ForegroundColor Yellow
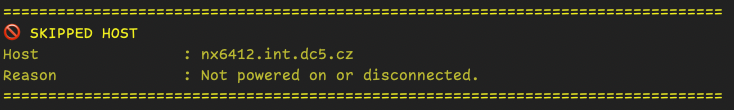
Write-Host "Host : $($esx.Name)" -ForegroundColor DarkYellow
Write-Host "Reason : Not powered on or disconnected." -ForegroundColor DarkYellow
Write-Host "================================================================================" -ForegroundColor Yellow
Write-Host ""
continue
}
$esxcli = Get-EsxCli -VMHost $esx -V2
try {
$key = $esxcli.system.settings.encryption.recovery.list.Invoke()
$enc = $esxcli.system.settings.encryption.get.Invoke()
Write-Host "================================================================================" -ForegroundColor DarkCyan
Write-Host "🔹 ESXi Host : $($esx.Name)" -ForegroundColor Cyan
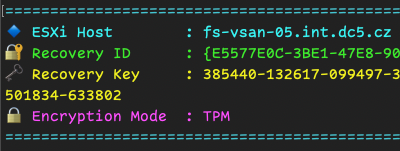
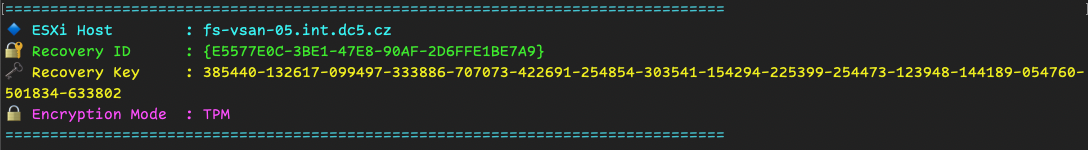
Write-Host "🔐 Recovery ID : $($key.RecoveryID)" -ForegroundColor Green
Write-Host "🗝️ Recovery Key : $($key.Key)" -ForegroundColor Yellow
Write-Host "🔒 Encryption Mode : $($enc.Mode)" -ForegroundColor Magenta
Write-Host "================================================================================" -ForegroundColor DarkCyan
Write-Host ""
}
catch {
Write-Host ""
Write-Host "================================================================================" -ForegroundColor DarkGray
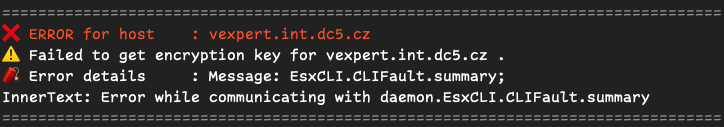
Write-Host "❌ ERROR for host : $($esx.Name)" -ForegroundColor Red
Write-Host "⚠️ Failed to get encryption key for $($esx.Name) ."
Write-Host "🧨 Error details : $_"
Write-Host "================================================================================" -ForegroundColor DarkGray
Write-Host ""
}
}What the Script Does
- Connects to each ESXi host.
- Checks if the host is Connected or in Maintenance mode.
- Retrieves the Encryption Recovery ID and Key.
- Shows the current encryption mode.
- Gracefully handles hosts that are offline or disconnected, clearly indicating skipped or problematic hosts.
Output
Connected hosts or in Maintenance with Encryption keys
Powered off or disconnected hosts – Skipped hosts
Hosts without encryption keys or with errors
Wrapping It Up
This quick script helps you stay on top of ESXi encryption keys effortlessly. Just copy, adjust if needed, and run. Happy scripting!